Covid-19 has stalled the world's economy, but one 'business' is booming. We examine the rise in cyber attacks and talk to the experts trying to prevent them
by Tim Green
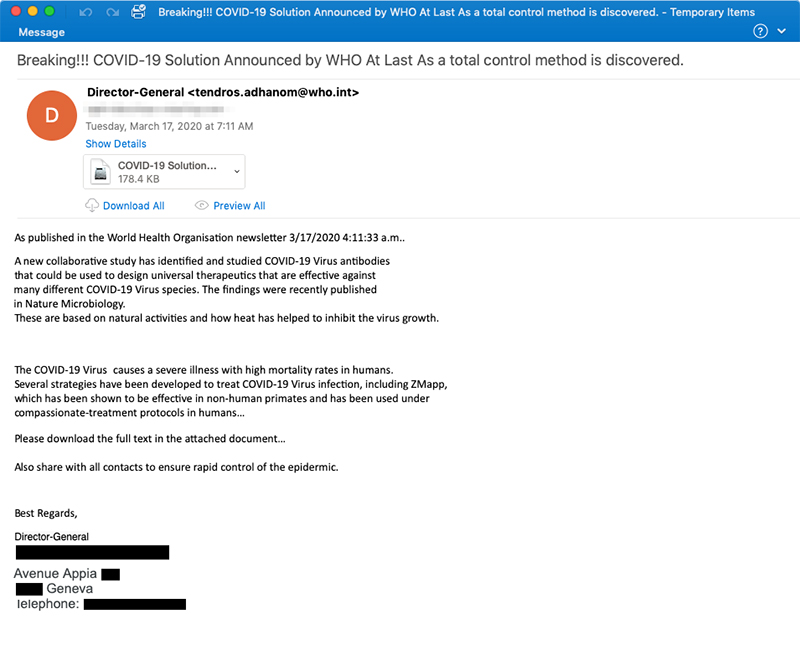
Would you respond to an email with the following subject header?
"Breaking! Covid-19 Solution Announced by World Health Organsation At Last As a total control method is discovered."
Probably not. The phrasing is inappropriate for a global health organisation. But the clumsy wording might be deliberate. According to a post on Joseph Steinberg's website (Steinberg is the author of Cybersecurity for dummies), fraudsters frequently use spelling and grammatical errors to ensure that only those who don't recognise the errors will respond. And, regrettably, cyber criminals have never been busier. Covid-19 might be slowing the commercial world to a crawl. But for scammers, it's a huge opportunity. Why? Because the virus gives them an angle.
Source: Proofpoint
In a study published on 27 March 2020, security specialist Proofpoint says it detected 500,000 messages, 300,000 malicious URLs and 200,000 malicious attachments with Covid-19 themes since 29 January 2020. And in a blog post published on 16 April 2020, Neil Kumaran, product manager, Gmail security, and Sam Lugani, lead security product marketing manager for G Suite and Google Cloud Platform, write about how busy Google had been over the previous week, detecting 18 million daily pandemic-related malware and phishing Gmail messages.
Source: Proofpoint
The pandemic gives the criminals many sources of official information to spoof. As governments around the world issue grants and rebates, scammers are mimicking them. And Covid-19 information overload and fear seems to have lowered the public's ability to spot the fakes.
IBM confirms this. Its April 2020 Consumer & small business Covid-19 awareness study finds that 52% of US citizens say they would click on links or attachments related to stimulus cheque eligibility. But Covid-19 grants aren't the only subject matter for the scammers. There have been phishing emails with attachments that claim to list neighbours with the disease, links to miracle cures and even offers of anti-bacterial credit cards. The latter email scam, which targeted Dutch businesses, contained a link to apply for this magical card. The fake landing page then harvested visitors' banking credentials.
The Global Cyber Alliance (GCA), launched in 2015 in an international cross-sector effort dedicated to preventing cyber attacks, is a collaboration between the City of London Police, New York County District Attorney and the Center for Internet Security. GCA's UK, India and Middle East executive director Andy Bates says that there is always an increase in attacks around disasters as "those perpetuating the attacks take advantage of social engineering opportunities to prey on people's fear".
He says that cyber criminals are taking advantage of Covid-19 to launch attacks to spread disinformation, commit financial fraud, and target the new 'work from home' workforce. "Interpol has reported seeing an increase in malicious domains with 'Covid-19' and 'Corona' embedded into the name." There have also been attacks against healthcare organisations, he says, which led the Cyber Peace Institute to develop the Cyber 4 Healthcare campaign to provide help and resources to organisations who need it.
Developments in cyber crime
This activity merely represents the latest spike in a cyber crime 'business' that is now eye-wateringly huge. In its 2019 report Managing cyber risk with human intelligence, Citi Global Perspective & Solutions (GPS) estimates that cyber breaches cost the global economy US$1.5tn per year. By 2021, it could be US$6tn. In a column for advisory firm Robinson Hambro, its CEO Karina Robinson, who is also Master of the Worshipful Company of International Bankers, writes: "The cyber security market is already worth around US$120bn, similar to the GDP of Morocco, while the cost of cyber crime is estimated at up to US$2tn."
This 'economy' emerged around 20 years ago when offices became more connected. Criminals saw an opportunity to spoof websites, local area networks, email and the other markers of a networked enterprise. Then, around ten years ago, employees began bringing their own technology to work. Suddenly, hackers were able to target employees' smartphones and tablets. The Citi GPS report says the number of internet users grew 100% from 2008 to 2018 while the number of websites grew 818% in the same time frame.
While it tends to be cyber attacks on big businesses resulting in the loss of millions that make the headlines, in a CISI TV interview with Robinson, Andy says that criminals have moved to easier victims – the consumer. "It is simpler to steal £100 from 100,000 people or small and medium-sized enterprises across hundreds of different legal jurisdictions than a million from a well-defended bank," he says.
Now we have the Internet of Things (IoT), we're connecting – but not necessarily securing – every kind of device: cameras, cars, doorbells. Even hoovers are not safe. In 2018, enterprise security specialist Positive Technologies identified flaws in the Dongguan Diqee 360 robotic vacuum cleaner. The vacuum has WiFi, a webcam with night vision and smartphone-controlled navigation, allowing a potential attacker to spy on the owner of the product.
Security experts despair at the mistakes being made by some IoT device makers. "You look at these products and you think 'have we learnt anything?'" says Jason Hart, security expert and CEO of Fresh Security, a cyber security solutions provider. "The manufacturers are using default passwords and out of date protocols. They're writing code in cleartext. And they're not hiring people who know about cyber security."
IoT has increased the threat of cyber attacks, says Andy Bates, with the devices becoming a vulnerability to the networks on which they reside. "There is a much larger attack space and the vast majority of the estimated 31 million IoT devices do not have good security, if any. Over the past several years we've seen baby monitors and toys compromised, printers and fax machines that are vulnerable," says Andy. He gives an example of a major IoT attack – the Mirai botnet. It launched a massive distributed denial-of-service (DDoS) attack [a cyber attack on a server/website/network that floods it with traffic rendering it unusable] by exploiting insecure TVs and home routers. This attack caused massive damage, yet DDoS attacks are still active today because of the number of unmanaged devices that are still connected to networks.
Worryingly, Jason believes the danger posed by IoT attacks will be graver and more insidious than today's computer-based breaches. "Most existing cyber attacks try to expose confidential data for financial gain. IoT attacks will be more about data integrity," he says. "Companies will rely on data from IoT devices to make important business decisions. The risk is that hackers will modify that data for their own purposes, and companies will have no idea until it's too late."

Cyber crime todayWhile tomorrow's cyber criminals work on these methods, today's equivalents are focusing on more straightforward stealing. According to the Citi GPS report, financial theft grew 93% in the US between 2017 and 2018.
How to improve your cyber hygiene
The Global Cyber Alliance believes most cyber attacks are unsophisticated. It says that basic cyber hygiene principles will deter the majority of them. To help businesses to apply these principles – especially when home working – it's created a toolkit comprising free advice, software and tools. Here are its main takeaways:
1. Know what you have – Identify all connected devices and applications. Keep an up-to-date inventory.
2. Update defences – Boost digital immunity against viruses, spyware and more by keeping systems updated. Configure systems to update automatically.
3. Use complex and unique passwords – All devices, accounts and applications should have a unique and complex password. The toolkit includes free tools for generating them as well as advice on setting up two-factor authentication.
4. Install anti-phishing and anti-virus systems – Malware attacks can infect systems, which costs money and can cause severe damage to reputation. There are free defensive tools in the GCA toolkit.
5. Defend against ransomware – Ransomware locks important data and demands money to unlock it. The obvious defence is to back up regularly – to a separate and unconnected storage centre.
6. Protect emails – Hackers use various tools to take control of official email addresses. The best protection against this is DMARC. It authenticates legitimate email, ensures genuine email does not go to junk folders and blocks hacked emails before they reach customers.
7. Avoid the use of public WiFi – Instead, use private home networks or mobile hotspots. If you have to log in to public WiFi, use a VPN.
8. Consider a privacy screen – Shoulder surfing is a real thing. Use a physical barrier to prevent criminals from spying.
Fraudsters often focus their attacks on individuals, using social engineering to trick their targets into downloading malware inside bogus apps or email attachments. Or they use brute force attacks that try millions of password combinations every second.
Evidence points to a huge rise in the number of credentials available to criminals on illegal markets. Research by cyber crime specialist Digital Shadows, published in July 2020, paints a bleak picture. The firm spent 18 months auditing dark web forums and identified 15 billion stolen credentials from 100,000 data breaches.
Jason believes the existence of these illegal markets make it even more important for people to be more vigilant. "It's pretty easy for criminals to buy up passwords in bulk," he says. "And the problem is that most people use the same passwords across multiple sites and never change them. So, when criminals buy these stolen details, they can do what we call 'credential spraying' to sign in to other accounts."
This is making it easier to launch more sophisticated attacks. Criminals can use stolen data, along with clues left on social media, to target particular individuals. These tactics can be extremely lucrative. In 2016, Sophos reported that a Mattel executive received an email from her CEO asking her to wire US$3m to a Chinese supplier. She did. But the email was fake. She sent the US$3m to a criminal gang.
A similar example, provided in the CISI's Cyber crime Professional Refresher, saw criminals target the Far Eastern International Bank (FEIB) in October 2017. They used a phishing attack to infect IT systems used to manage the SWIFT payment network. They then attempted to transfer US$60m. Thankfully, most of the messages were misconfigured, so total losses were estimated at less than US$500,000.
Then there was the WannaCry ransomware attack on the NHS in May 2017. Here, criminals exploited a weakness in older versions of Windows OS, and demanded a ransom to be paid in Bitcoin.
Staying ahead of the cyber criminals
Experts advise that basic self-protection can deter most attacks. The GCA has several solutions available, including a free toolkit that helps business owners reduce cyber risks. It says the measures can reduce risk by 85% (see boxout). It also has a protective DNS service that prevents users from visiting bad websites and also offers DMARC, an email authentication protocol, which is configured to secure a website against email abuse. It essentially stops hackers from impersonating an email address. According to the GCA, HMRC.gov.uk used to be one of the top ten most spoofed email addresses, with 500 million annual emails posing as HMRC. DMARC has all but eliminated this activity
Quad9 is another GCA solution for both companies and individuals, which blocks against known malicious domains, preventing your computers and IoT devices from connecting to malware or phishing sites. It currently protects an estimated 200 million users and stops 100 million cyber crime attacks daily, according to the GCA, and takes only one minute to configure. The GCA reports that people who implement Quad9 see an 80% reduction in attacks seen by systems such as their virus scanners.
According to Jason, good internal policy can go a long way to defending against attacks. "Many companies don't have any kind of password guidelines for staff. But ensuring people use strong passwords, and change them regularly, can make a big difference."

He adds that two-factor authentication with one-time passwords offers even better protection. Typically, this would involve sending a randomly generated PIN to be entered into a phone. And if the phone itself is accessible only with a fingerprint or facial recognition, even better.
In April 2020, the UK Defence and Security Accelerator (DASA) awarded £1m to three companies to develop technology that predicts and counters cyber attacks. And in May 2020, the UK government launched a virtual cyber school for teens, offering free weekly webinars on digital forensics, cryptography and operating systems, with the goal of encouraging young people to join the fight against internet crime.
While individual countries pursue their own cyber security schemes, experts know that cross-border initiatives are the key to fighting the most organised criminals. GCA is one example but there are many more. The United Nations has a global programme to help members coordinate their work on cyber crime. Its stated aims are to speed up the investigation, prosecution and adjudication of cyber crime, help members with data collection and legal frameworks, and improve communication between government, law enforcement and the private sector. And in 2019, the EU passed the Cybersecurity Act (CSA) and created the European Union Agency for Cybersecurity to enforce it.
"There's a growing 'crime as a service' economy. We have to do all we can to stay one step ahead"The virtual, dispersed nature of cyber crime poses a challenge to police forces worldwide. Mike Hulett, head of technology and capabilities at the UK National Cyber Crime Unit (NCCU), part of the National Crime Agency, explains: "It's harder to do traditional detection and evidence gathering when the criminals are on the other side of the world, and don't even know each other's real identities. Also, they can obfuscate so easily – by transacting on the dark web or by using virtual currencies."
Mike estimates more than half of all UK crime is now cyber crime when you include all the cyber-enabled fraud that is committed, and he agrees that the perpetrators are choosing their targets more deliberately, for example, the shutdown of Britain's largest private forensics provider, Eurofins. According to news reports, it paid an undisclosed ransom after an attack last year. "There's less 'spray and pray' now," says Mike. "Criminals are more strategic. They will do things like time a strike on a company when there's a new share issue or a merger – when the board is looking the other way.”
Agencies such as the NCA accept they are in a constant race to stay ahead of the cyber criminals. They also know that every tool developed to fight back can be turned against them. Take AI. Tools such as ThetaRay's IntuitiveAI can analyse huge amounts of customer data to detect anomalies that might reveal fraud. But it seems inevitable that criminals will adopt the same techniques.
A World Economic Forum article written by William Dixon, head of operations, Centre for Cybersecurity, World Economic Forum and Nicole Eagan, CEO of Darktrace, speculates that AI could make phishing much more effective. It reports: "By leveraging an AI's ability to learn and replicate natural language, an AI-powered trojan could create and insert entirely customised, more believable phishing emails. Crucially, it would be able to send these out at scale, which would allow criminals to increase the yield enormously."
Over time, these tools will become cheaper and easier to use. Mike is already seeing evidence of a 'cyber crime to order' market, which might trigger the next proliferation of activity. "It's getting easier to hire people to commit these kinds of attacks. There's a growing 'crime as a service' economy. We have to do all we can to stay one step ahead," he concludes.